LDAP and ACL Synchronization
LDAP Sync
This feature will be released with version 10 "Heisenberg" of the PowerFolder Server.
PowerFolder Server allows the Administrator to import Accounts, Groups and Organizations from an existing LDAP/Active Directory server.
As of version 10 "Heisenberg", the Preferences page contains new input fields:
- Synchronize server structure periodically (checkbox)
Organizations:
- Organization mapping (drop down list)
Automatic import of LDAP/Active Directory
![]() Preferences → Authentication → LDAP / Active Directory → Import LDAP structure
Preferences → Authentication → LDAP / Active Directory → Import LDAP structure
The PowerFolder Server is now able to import your LDAP/Active Directory Accounts, Groups and Organizations.
Accounts
Accounts are identified by having the attribute objectClass set to person but they must not have set objectClass to computer as well.
Accounts must apply to some criteria to get imported:
- The Account must not be disabled
- The Account must not have the same name as the account searching the LDAP/Active Directory
- The Account's username must not start with
"sm_"as those are system Accounts
Groups
Groups are identified by having the attribute objectClass or objectCategory set to group.
Groups are imported during the process of importing Accounts. Accounts have an attribute "memberOf" which identify a group they are member of. Only those Groups are imported. This ensures only populated Groups to be imported empty Groups are not imported.
This feature of version 10 "Heisenberg" only imports Groups that have Accounts as members directly, but not those that contain only Groups. PowerFolder is not able to have Groups containing Groups.
Organizations
For the Organization mapping there are six values to choose from:
- No mapping No Organization will be imported
- Single Domain (1) Use if your LDAP/AD has a top level node of example.com with no subdomains (on the first node)
- Multi Domain (2) Use if your LDAP/AD has a top level node of example.com with subdomains (sub nodes) e. g. ny.example.com, berlin.example.com, tokyo.example.com ... (on the second node)
- Other (3) Use if your LDAP/AD has the Organizations you want to import as a sub node of a multi domain setup e. g. the first node under berlin.example.com (on the third node)
- Other (4) Use if your LDAP/AD has the Organizations you want to import as a sub node of a multi domain setup e. g. the second node under berlin.example.com (on the fourth node)
- Other (5) Use if your LDAP/AD has the Organizations you want to import as a sub node of a multi domain setup e. g. the third node under berlin.example.com (on the fifth node)
The Organizations are classified according number of commas in the Distinguished Name of the node (it must have the exact amount of commas) and if the left hand side begins with one of the following:
- ou Organizational Unit
- o Organization
- dc Domain Component
Periodic synchronization of LDAP structure
The periodic synchronization of LDAP/Active Directory will be started every hour.
New accounts will be imported, attributes of existing accounts will be updated, but no accounts will be deleted, that are deleted in the LDAP/Active Directory. Group membership will be updated as well. If a Group has no members anymore, it will not be deleted. When LDAP synchronization is executed and finished, following will be stored in PowerFolder-Server logs:
Server logs
"Starting import of up to " + maxNumberOfAccounts + " accounts from " + ldapServerURL
"Imported " + numberOfAccountsImported + " of " + maxNumberOfAccounts + " Accounts"
When Organizations are imported, their number of maximum users and space limit are set to "unlimited". Also, no Organization Administrator Role will be set automatically.
ACL Sync
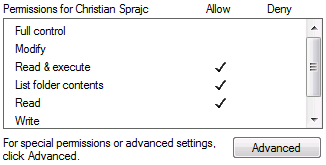
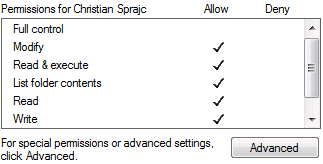
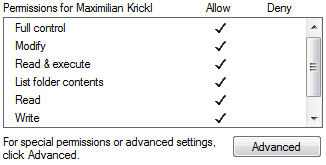
Permissions are read from the base path of the Folder and transferred to PowerFolder permissions for users and groups. For users, the PowerFolder Server sets the ACLs on the filesystem according to the PowerFolder permission.
Permissions for groups are not synchronized back to the filesystem.
The mapping of Folder Permissions to NTFS Permissions is done as follows:
| PowerFolder Permission | Read | Read/Write | Admin | Owner |
|---|---|---|---|---|
| NTFS ACL Entries |
|
|
+ Set the user account as owner | |
| NTFS ACL Flag |
|
The Folder Permissions are in ascending order of permissions, a Folder Permission inherits the permissions from all other permissions on the left.
Get certificates of SSL enabled LDAP Server and import them in java cacerts
If the LDAP users are unable to login and as server admin, the following logs are occurring:
Root exception is javax.net.ssl.SSLHandshakeException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target] / de.dal33t.powerfolder.security.AuthenticationFailedException:
Please follow the guide: https://knowledge.informatica.com/s/article/HOW-TO-Get-certificates-of-SSL-enabled-LDAP-Server?language=en_US