Federated Clouds
Table of contents
Intention
The concept of a Federated Cloud within PowerFolder aims to combine installed PowerFolder Services on several locations to seamlessly share and sync files between end-users of those services.
Overview
Users of different organizations, that already use a PowerFolder Service at their location, should get enabled to access other organization's data by sharing Folders instead of sharing File Links. Thus allowing them to share data with end-users to that organization. Files should be accessible via the web interface, the PowerFolder Client connecting to different services at all participating organizations and the PowerFolder Mobile App. Every organization should stay in control of their user administration. Users are authenticated by their home institution. A Trust Relationship has to be established between participating organization's services. This enables system administrators to decide which systems to connect to.
Use cases
 User A (Hosted on Cloud X) wants to share files with User B (Hosted on Cloud Y).
User A (Hosted on Cloud X) wants to share files with User B (Hosted on Cloud Y). User wants to access files from two or more PowerFolder Cloud Services by web portal
User wants to access files from two or more PowerFolder Cloud Services by web portal User wants to sync files from two or more PowerFolder Cloud Services by client.
User wants to sync files from two or more PowerFolder Cloud Services by client. User wants to sync and access files from two or more PowerFolder Cloud Services by mobile app.
User wants to sync and access files from two or more PowerFolder Cloud Services by mobile app.
Requirements
- Installation of PowerFolder Version 11 or higher at all participating services:
- Server with version 11.5 aren't compatible with versions below.
- Server with version 11.6 aren't compatible with versions below.
- This documentation is for server with PowerFolder version 14.6 and higher.
- At least the following Cyphersuite should get used:
ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS
Preparation
- Set the config Parameter "server.federation.login_enabled=true" in the PowerFolder.config file of your server. Restart your server afterwards.
- Ensure that your server has a valid TLS certificate and can get accessed via HTTPS. HTTP only is prohibited for security reasons.
- Ensure that your web ports and your data ports can get reached by the federated servers and their clients.
Setup
- Login as admin and navigate to "Federation".
- Add a federated service simply by entering the service URL on top and click "Add":
- Your server will request mutual trust with the federated service. Their admin just has to accept your invitation.
- Make sure that all services that are working with you accept your invitation.
Note:
- For testing purposes a federated service is running at https://my.powerfolder.com/federation.
- Please contact us for enabling mutual trust for your service.
Ready! Now that all services joined the same federation and enjoy mutual trust, sharing files and folders between user's across all services is possible.
Login for users
A user can log in on any federated service. When he enters his Username/E-Mail he will get redirected to the correct service where he can enter his password.
For this purpose the login page got modified to only accept the username and after finding the account the password field shows up.
User Accounts
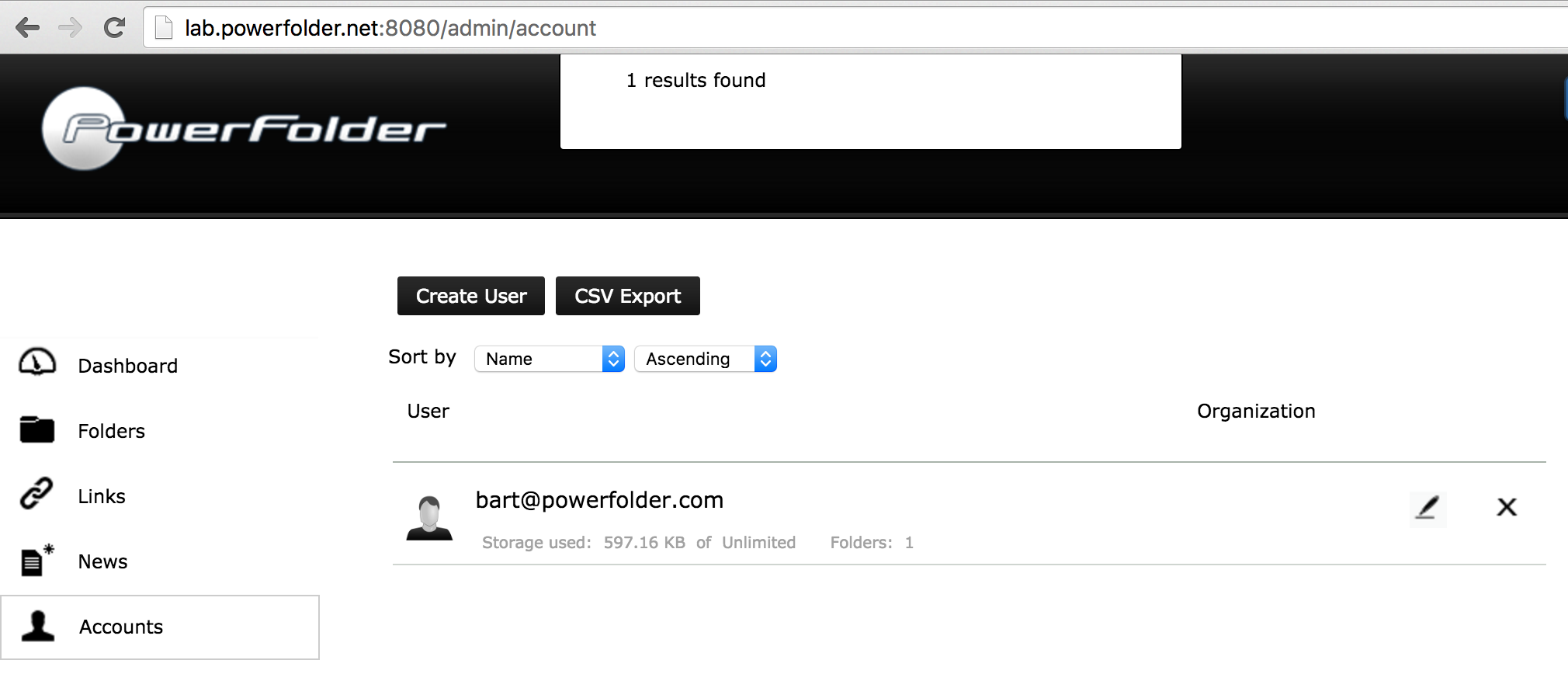
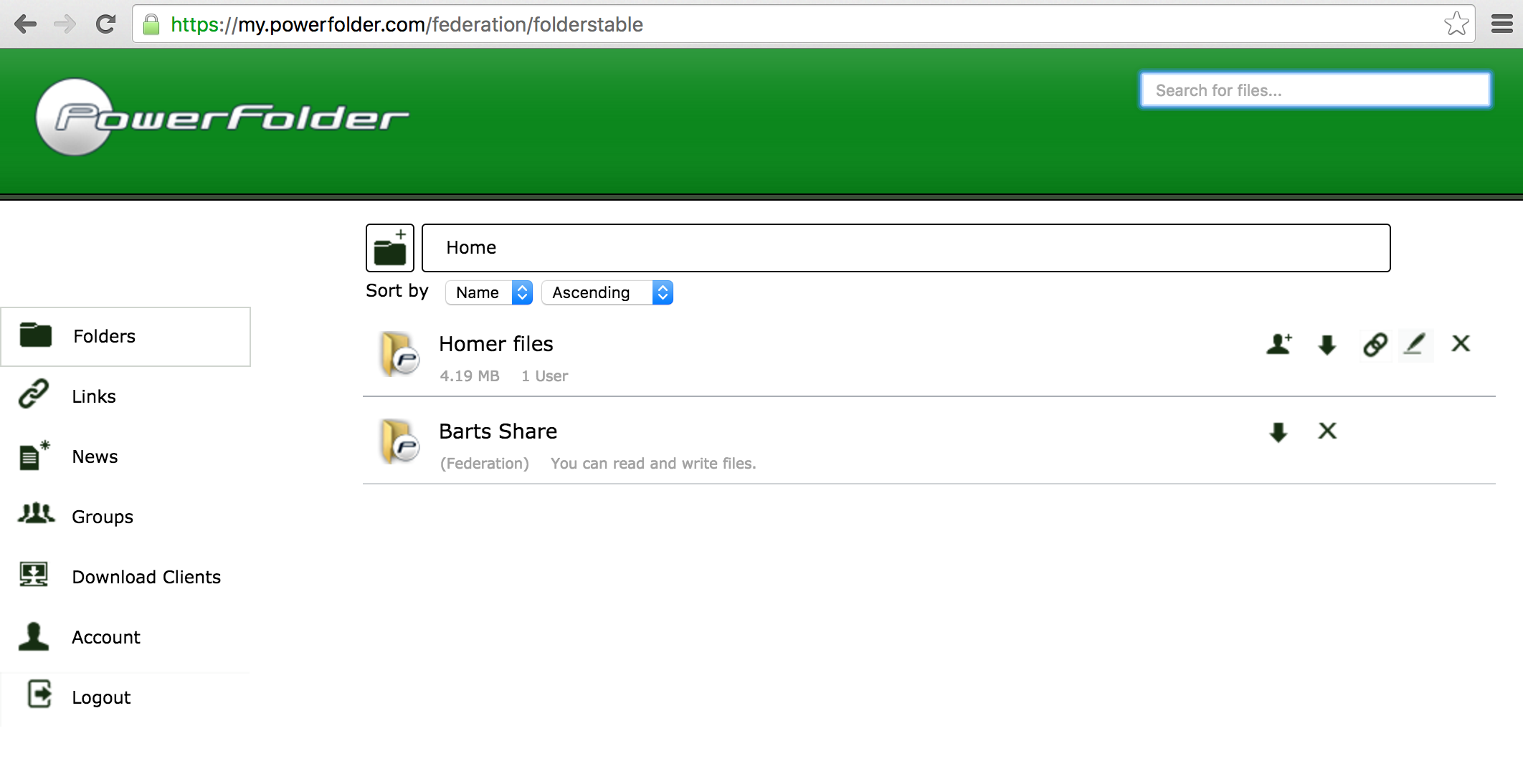
In this example there is one local user account (bart@powerfolder.com) on the "black" service:
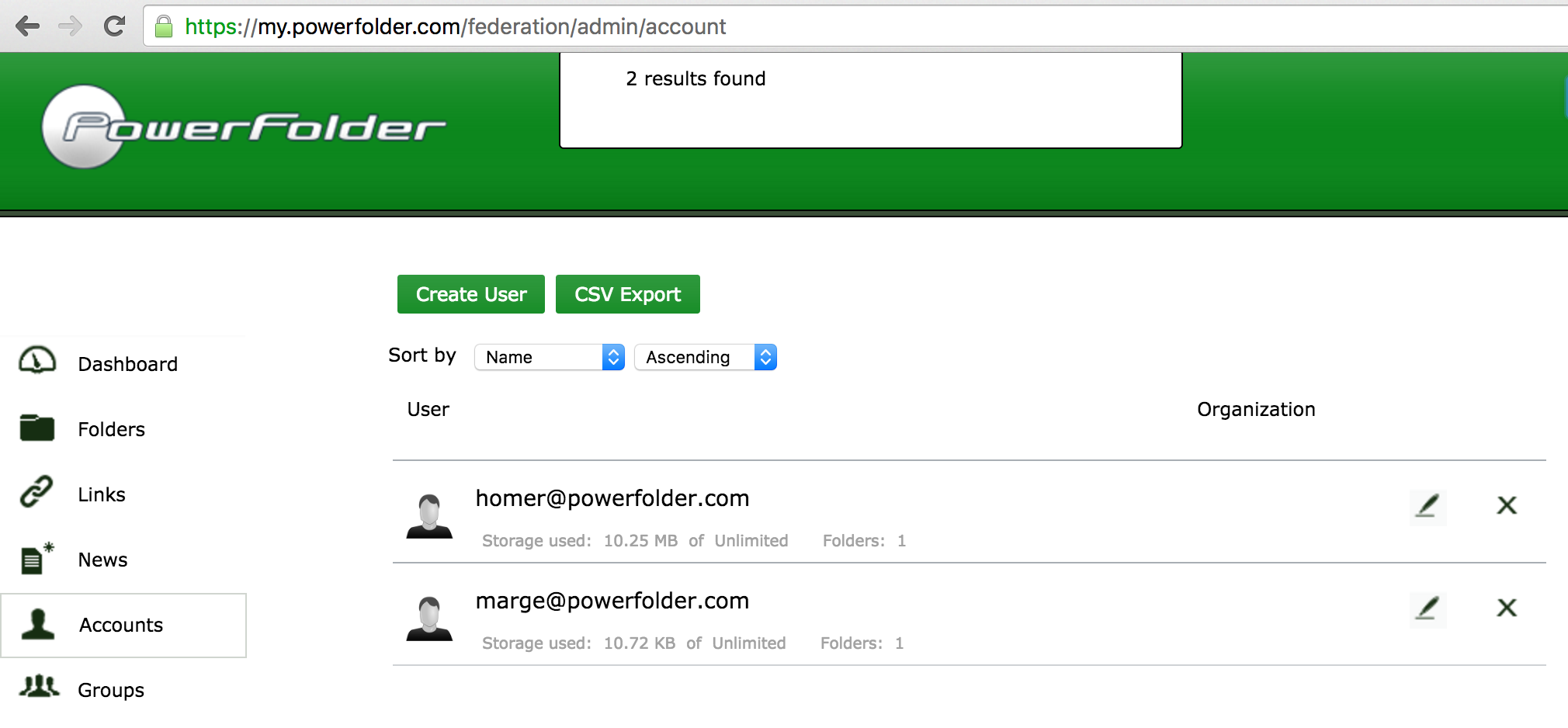
and two accounts (marge@ and homer@powerfolder.com) on the "green" service:
Both services have joined the same federation and established mutual trust relationship.
Sharing folders
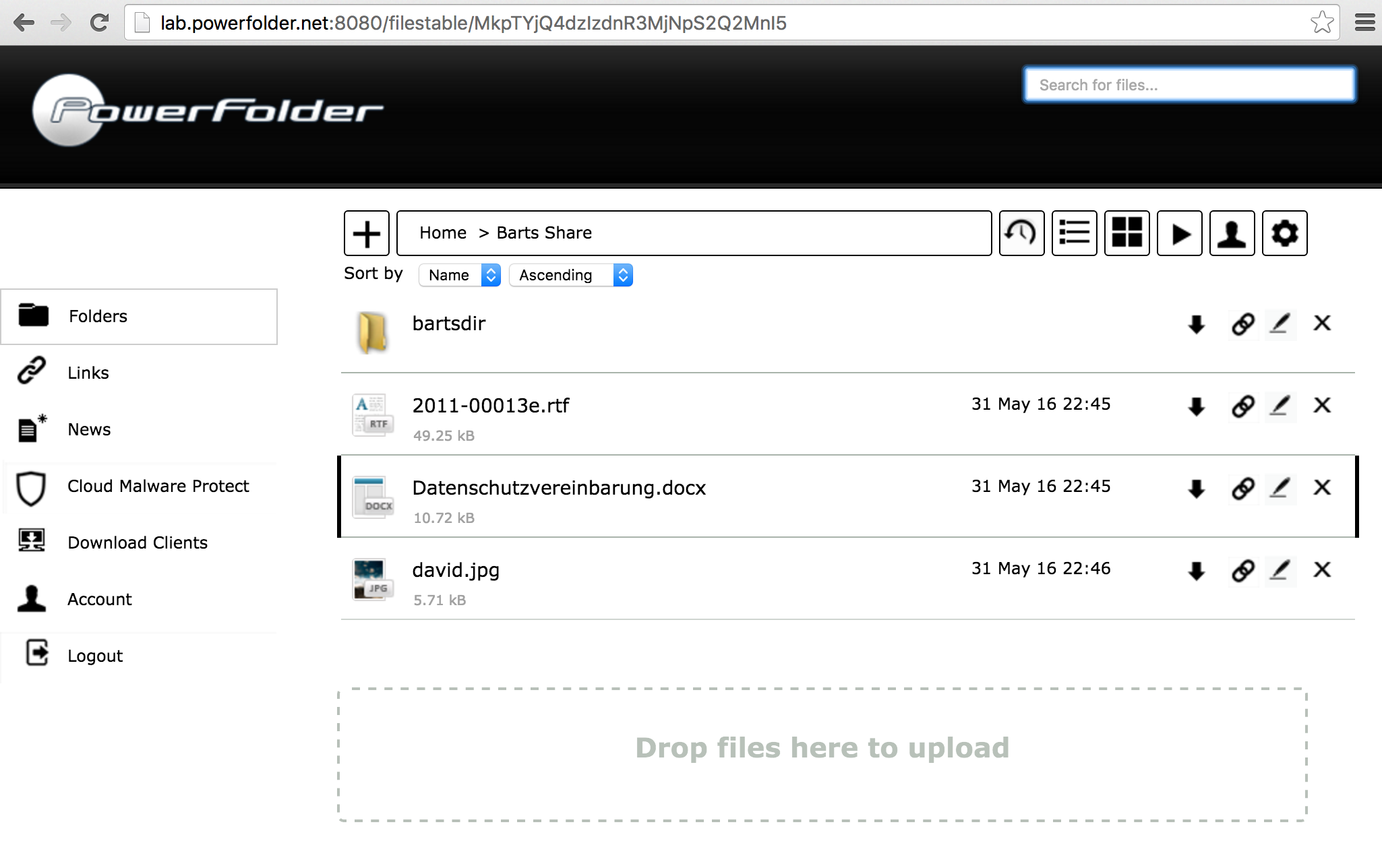
Login as user and navigate to the folder to be shared (bart@powerfolder.com at black service):
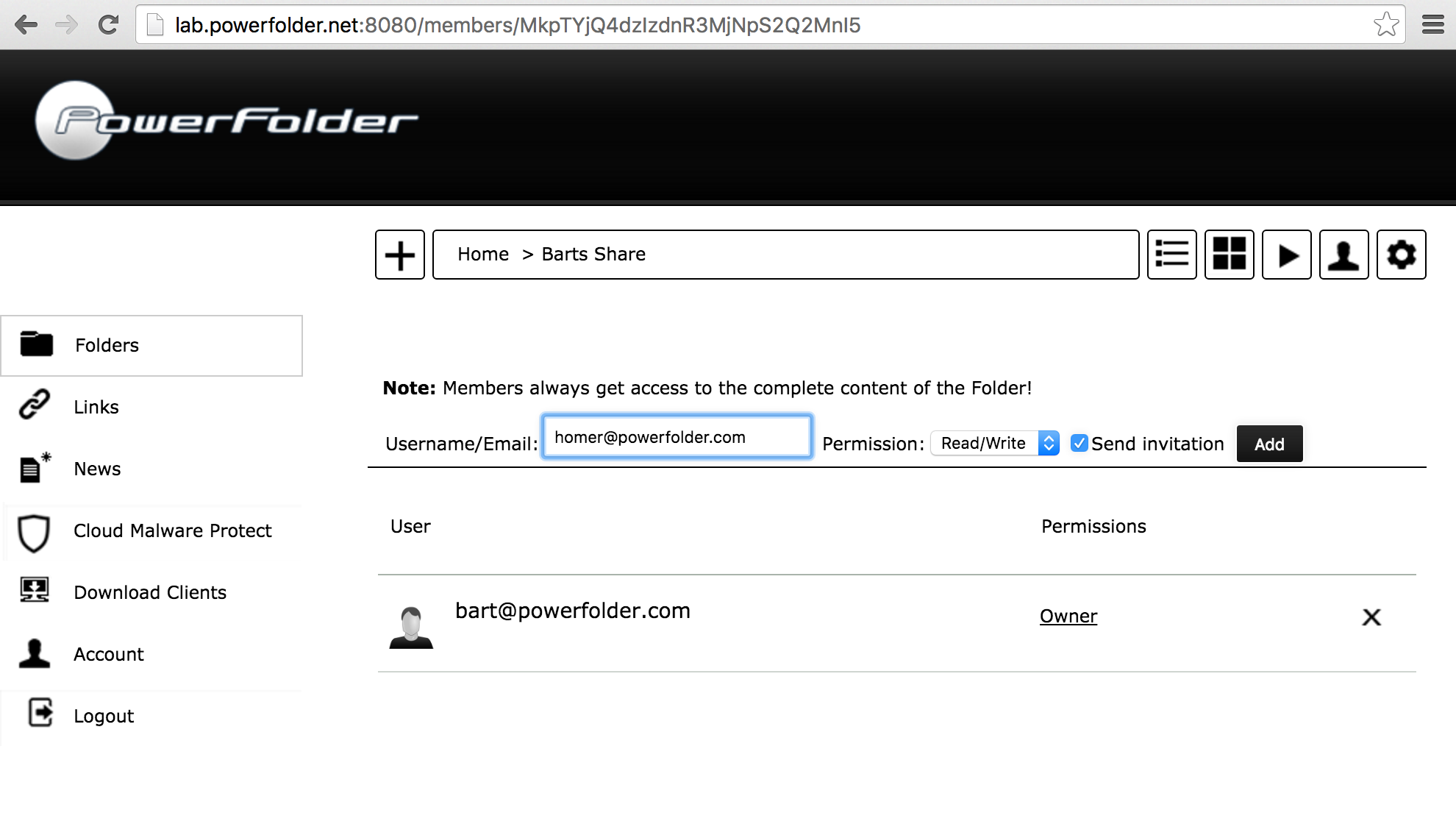
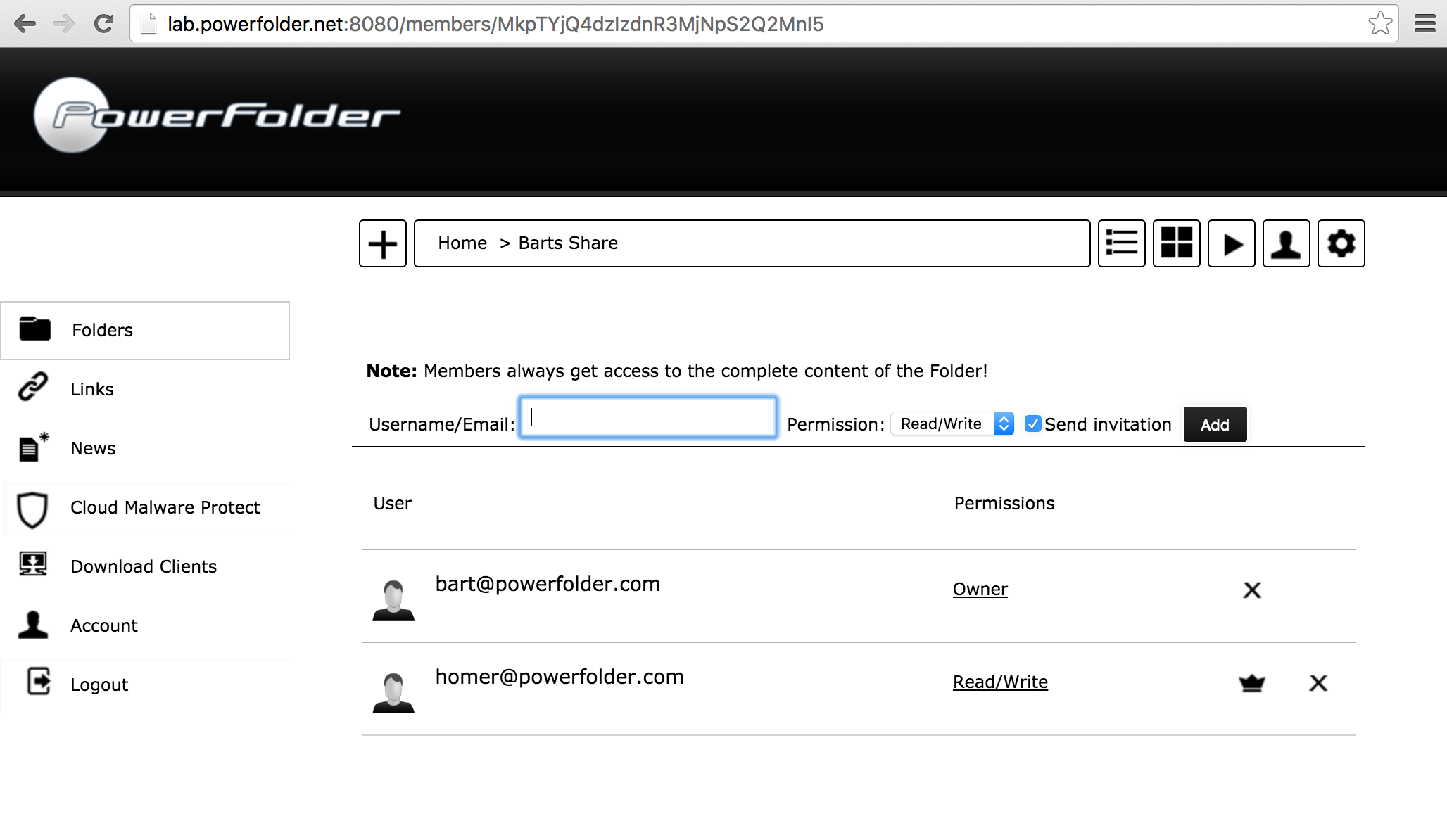
- Navigate to the members list:
- Enter the email address of a user hosted on a federated service (homer@powerfolder.com at green service)
- Press "Add". The invitation will be send to the federated service and the user shows up:
Accessing shared folder
- On the target service (green service) login as recipient user of the invitation (homer@powerfolder.com)
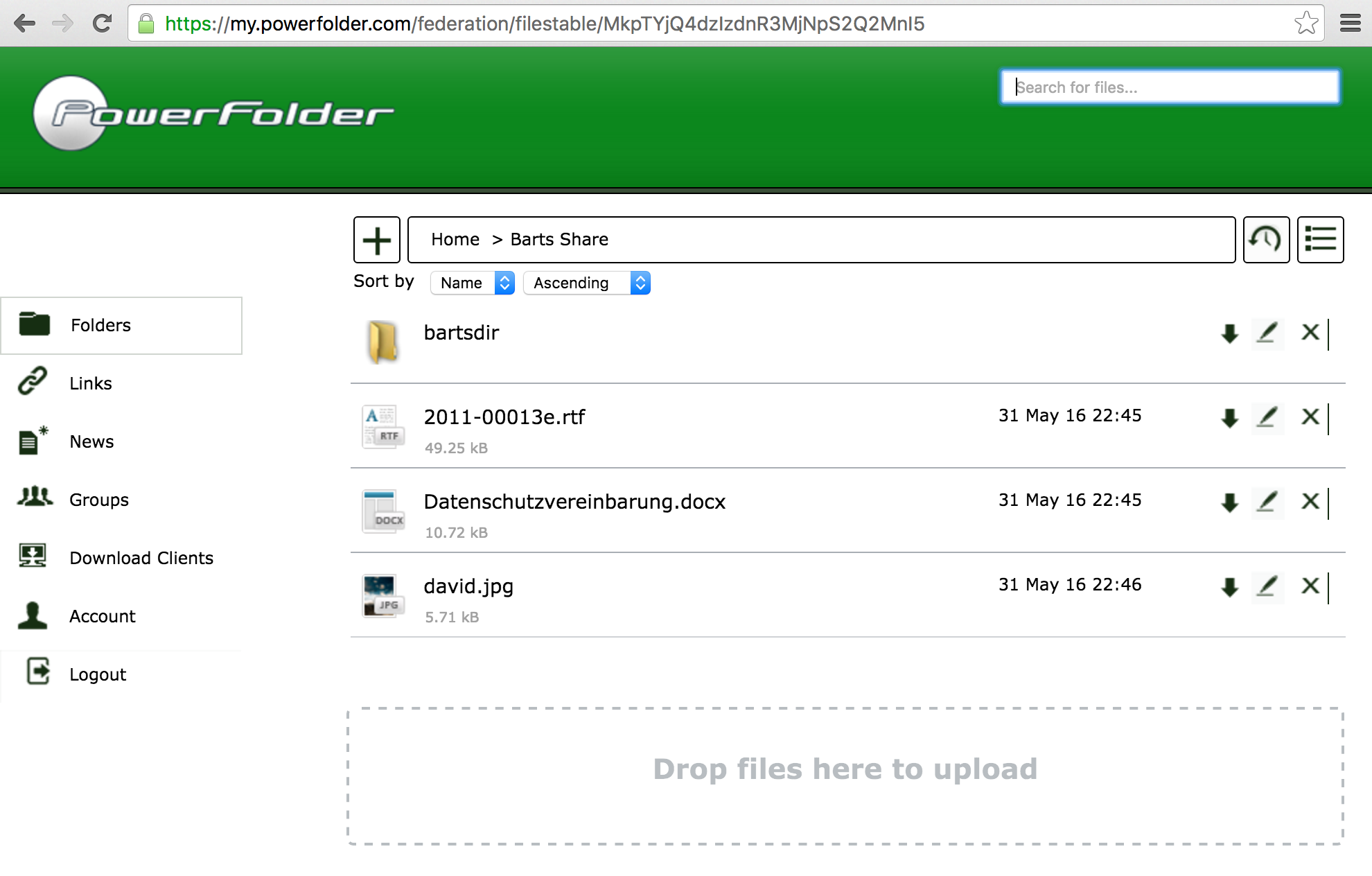
- The shared folder will show up in the list indicating, that it's shared within the federation:
- Click on the folder to access its contents:
Et voilá! The two users just shared a folder across two services within the federation. The recipient may now list, download, rename, delete, restore, create and upload contents.
Known Issues and Restrictions:
Currently the federation has some known issues:
- Federated proxy accounts can get merged by other accounts, when they add the external mail address to their own account. All future invitations will be handled locally.
- At the moment for every mail address a proxy account gets created. Even if it is the same user.
- Permission management is not possible. When inviting a user initially the permission can get set but not changed. Only R/W and Read Only are possible!
- Deleting permissions on the hosting service doesn't delete the folder on the federated service, but files aren't accessible any longer.
- When the user on the federated system leaves a folder he is not deleted in the member list on the folder in the hosting system.
- When a federated service has dynamic folder mounting activated the client might not be possible to connect to the folder of this federated service until a user logs in who has direct access to the folder.
- The function to show files in web is not working automatically on a federated folder.
- Adding the services on both sides results in no invitation to accept the mutual trust. Please only add a service on one side and accept it on the other.
Feedback
Your feedback is urgently needed to extend and harden out the federated cloud sharing feature. If you encounter problems or have recommendations please provide the following information if possible:
- Set file logging level to FINE
- Enable logging of web requests
- Support Packages of servers
- Step by step description on how to reproduce the problem
- Related screenshots
You may contact us with the online support portal