- Release Date: September 2023
- Build Number: 20.0.105
- Type: Hot Fix Release
This release contains major security fixes, please upgrade your server as soon as possible.
Download Links
- Linux
- Windows
Upgrade Information
- Please read this complete Release Notes and instructions before upgrading.
- Please follow the regular upgrade documentation for Windows or Linux
- Upgrading any previous version higher or equal to version 16.0.100
- Cluster: Running different versions on the servers in the cluster is supported but limited to version >= 16.0.100
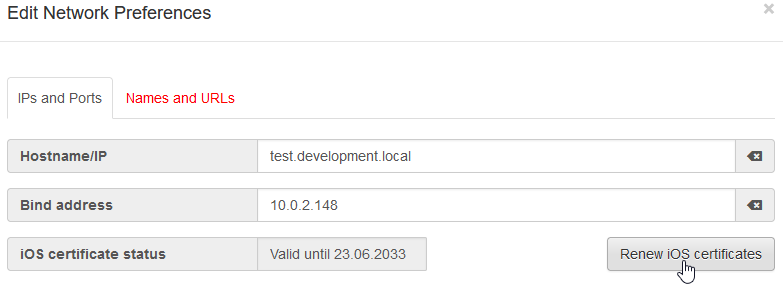
 Please renew the D2D certificate manually in the server preferences under "Network"
Please renew the D2D certificate manually in the server preferences under "Network"
Downgrade Information (optional)
- In case a downgrade to a previous version is necessary:
- For a downgrade you have to review our downgrade documentation.
- Simply replace the PowerFolder-Server.jar file with that from the previous version you would like to run.
- Log messages due to the higher schema version of database can be ignored:
[DatabaseMigrator]: Database layout version is newer than expected.
Improved Security
Overview: We are excited to announce with this software version, which comes with comprehensive enhancements aimed at addressing the OWASP Top security vulnerabilities. This release underscores our commitment to providing a secure and robust software solution for our users.
Key points:
Injection Attacks: We have implemented additional strict input validation and parameterized queries across the application to mitigate the risk of injection attacks, such as SQL, NoSQL, and Command Injection.
Broken Authentication: Enhanced authentication mechanisms have been integrated, including multi-factor authentication (MFA) support and improved session management, effectively reducing the threat of unauthorized access.
Sensitive Data Exposure: Our software utilizes strong encryption algorithms for data in transit. Additionally, sensitive data such as passwords and personal information are stored using industry-standard secure hashing methods.
Broken Access Control: Granular access controls have been refined, restricting users' permissions to only the necessary resources. Role-based access control (RBAC) has been expanded to ensure proper authorization throughout the application.
Security Misconfigurations: The default configurations of the software have been hardened to minimize potential vulnerabilities. Comprehensive security guidelines and best practices are now provided to assist administrators in configuring the software securely.
Cross-Site Scripting (XSS): Output encoding has been systematically implemented to prevent XSS attacks. Moreover, modern security libraries have been integrated to sanitize user inputs effectively.
Insecure Deserialization: We have adopted secure deserialization practices to thwart potential attacks. The software validates incoming serialized data and incorporates additional integrity checks.
Insufficient Logging & Monitoring: Our software now robust logging mechanisms, tracking both normal and abnormal activities. Real-time monitoring alerts have been set up to detect suspicious patterns, ensuring prompt action against potential threats.
Security Testing: To ensure the effectiveness of these security enhancements, rigorous testing processes, including static code analysis, dynamic security scanning, and penetration testing, were conducted throughout the software development lifecycle.
Upgrade Process: Upgrading to Version 20 release is strongly recommended for all users.
We remain committed to prioritizing security in all our software releases and will continue to collaborate with the security community to identify and mitigate emerging threats. Your feedback and vigilance are instrumental in our ongoing efforts to provide a safe and reliable software solution.
Thank you for choosing our software, and we look forward to your continued partnership.
Multi-Factor Authentication
PowerFolder web interface provides the multi-factor authentication (MFA) to enhance the data security and access the data everywhere after identifying the genuine identity of the owner and user of the data.
- Enabling MFA as server admin, please follow our documentation: Multi-Factor Authentication (Enable & Reset)
- User guide: Multi-Factor Authentication
Improved Speed of HTTP Connections
New defaults in PowerFolder.config:
transfers.max.file.chunk.size=131072
transfers.max.request.queued=30
Recommended Minimum Client Version
For security reasons It is recommended to set the minimum client version to v17.0.100 to connect with your server in the PowerFolder.config using the following configuration entry:
net.version.minimum=17.0.100
Changes
- PFS-4208 - High database load and fixes for several WARN and SEVERE logs
- Release Date: August 2023
- Build Number: 20.0.100
- Type: Major Software Release
Changes
- Security fixes for ONLYOFFICE
- Logging improvements
- INT-672 Fixed auto-complete in invitations and improved admin account edit method
- INT-672 - Authorization Framework to protect against potential future broken access control (OWASP No 1 of Top 10 Web Application Security Risks)
- PFS-4206 - Fix unable to update folder owner permissions
- PFS-4207 - Fix HTML support in TOS
- INT-674 - Hardened XSS Framework additionally implemented to prevent Cross-Site-Scripting vulnerabilities (OWASP No 3 of Top 10 Web Application Security Risks)
- PFS-4179 - Additional authorization check on /open urls
- PFS-4132 - Cosmetics with MFA, federated login and organization dropdown
- PFS-4127 - Disable username field, Reset button should return to login with username input
- PFS-4180 - Fixed Access Token update failure in federation after merge
- PFS-4185 - Prevent login pingpong: Account discovery now considers service name for DB accounts with same last activity date
- PFS-4181 - Account discovery in federation: Weight migration status when using LDAP
- PFS-4182 - Mount folders in federated server-to-server sync during service migration
- PFS-4195 - Automatically create and assign Accounts to Organization in LDAP
- PFS-4168 - Unable to update file links settings when expiry date is set by server admin
- PFS-4176 - Correctly handle access in federation when merged accounts have valid till set
- PFS-4187 - Merge account by email fixed in federation
- PFS-4184 - Take over folder ID from config if mismatching FolderInfo-File
- PFS-4192 - Performance Reduced number of threads and load caused by lot empty folders
- PFS-4188 - Reduce time threads are blocked due to concurrent access to config
- PFS-4189 - Top-Level-Folder do not show up under rare concurrent action
- PFS-4186 - Do not set storage path for proxy accounts
- PFS-4190 - Fixed Rejected federation request warning messages
- PFS-4191 - Disable HTTP Debugging Method TRACE
- PFS-4178 - Show changing account in news